18 December 2020
Password Trends in 2020
The pandemic has affected us all in one way or another. It was a tough year: as authorities around the world started issuing stay-at-home orders, we had to spend most of the year in our homes under long periods of lockdowns, and more and more people started working from home. And with it, the traditional password paradigm has come under scrutiny once again and we decided to take a look at the password trends in 2020.
As companies had to rely on a workforce that worked from home, they faced new challenges regarding cybersecurity. Most turned to remote access systems like VPNs to keep the gears turning, and it brought additional risks of potential data breaches. Most home setups lack the infrastructure and professionally managed networks that safeguard the employees, and this opens new attack vectors like unsecured or poorly secured home networks and devices. This certainly didn’t help matters, as employees often use their own networks and devices to continue working, which are managed by themselves.
The most commonly used passwords in 2020
2020 may have been one of the most challenging years to date, and it brought a lot of changes to the way we live. But some things don’t change and one of them is choosing poor passwords.
A recent study done by Nordpass revealed what the most commonly used passwords are in 2020, once again showing that easy-to-remember and easy-to-guess passwords are still popular as ever.
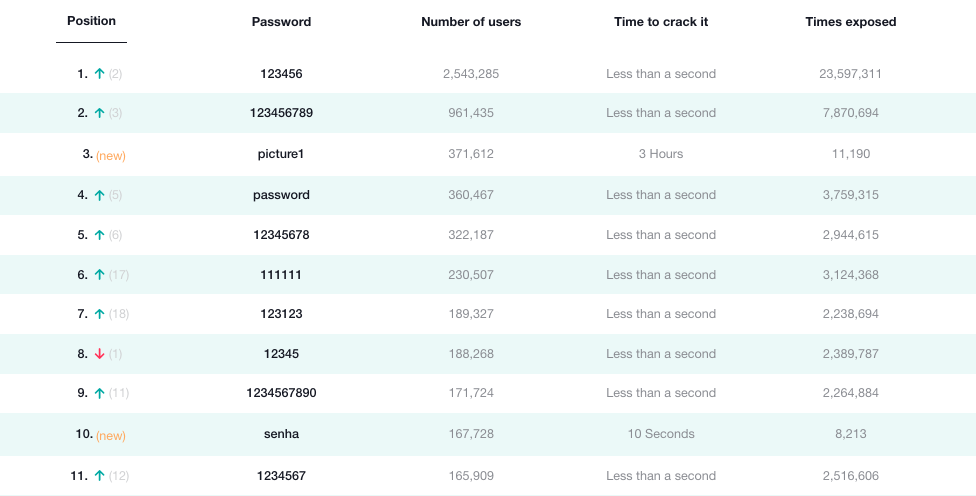
According to NordPass’s research, seven out of the top ten passwords are comprised of very similar numerical combinations, “123456” taking the lead. “picture1” and “senha” are new additions to the top ten list, with “senha” meaning “password” in Portuguese. The top 5 passwords on the list are used by over 4.5 million users, and they’ve been exposed over 38 million times in various data breaches in 2020. Keep in mind that these are known only because the exposed passwords are bought and sold on the black market, and surely there are more users out there using these passwords.
Phishing scams are on the rise
It’s clear that passwords aren’t safe. They haven’t been safe for a long time, and we see this same trend year after year where users opt for easy-to-remember passwords and have a false sense of security, and malicious actors know this.
Since the start of 2020, Google has detected over 2 million phishing sites. This figure is roughly 20% higher compared to last year, hinting at the opportunities the COVID-19 pandemic has given to scammers. According to the Google Transparency Report, 46,000 new phishing sites popped up every week on average in 2020.
Taking advantage of the fear caused by the pandemic, scammers send millions of fraudulent e-mails, tricking people to click on their links, taking them to their spoofed websites. These phishing sites often masquerade as real websites to dupe users into typing in their username and password combinations. According to BBC, scammers are sending 18 million of these COVID-related scam e-mails every day.
A stark revelation
At the RSA security conference in February 2020, Microsoft engineers stated that almost all of the compromised Microsoft accounts weren’t using multi-factor authentication. According to the speaker, roughly 0.5% of all accounts were compromised, which translates to 1.2 million accounts. Of all those cracked accounts, only 11% of them had a multi-factor authentication option enabled.
According to Microsoft, the most common method of attack was password spraying, which is trying to guess the password using a most commonly used password list. Following this, malicious actors use “credential stuffing”, where attackers attempt to gain access by trying usernames and passwords that were previously exposed in another data breach.
A panacea for all password problems
All of the above can be avoided by implementing a multi-factor authentication solution. Passwords have not been secure for a long time, and the future doesn’t bode well for this paradigm. It’s up to the companies to secure the accounts of their users, as users generally too reckless or inattentive to the security of their accounts. Businesses have to rely on a different way of verifying their users. That’s why setting up a multi-factor authentication solution is a must in this day and age, because passwords don’t cut it anymore.
However, there are costs associated with multi-factor authentication. When an app or a website decides to go that route, they’ll need to verify the users using a unique phone number, which is only associated with the individual user. For an MFA system to work, they’ll have to send an SMS to that phone number, identify the user, and let them log in. The thing is, SMS is costly, and their prices differ from region to region and it’s dependent on a multitude of phone carriers. When you’re verifying thousands of logins every day, it’ll add up very quickly very soon.
The good news is, it is costly if you only opt for SMS to verify your users. This is where VerifyKit comes in. With VerifyKit, you can verify your users via popular messaging app WhatsApp in addition to SMS, reducing your verification costs compared to traditional SMS. Check VerifyKit out today and start verifying your users today.
Share